`
`CyberSecurity | Business Intelligence:
Cybersecurity Infrastructure Consulting: the measures taken to protect a computer or computer system (as on the Internet) against unauthorized access or attack.
Cybersecurity requires coordinated efforts throughout an information system. Elements of cybersecurity include: * Application Whitelisting; Multi-factor Authentication, Security Information & Event Monitoring (SIEM)
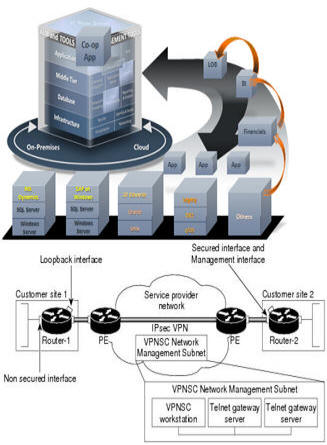
Infratac consultants can assist industry standard Busiess Intelligence (BI) REST API & security infrastructure design, implementation guidance & security threat mitigation best practices


CyberSecurity Infrastructure Design—Patterns & Practices
Business intelligence (BI) is a technology-driven process for analyzing data and delivering actionable information that helps executives, managers and workers make informed business decisions.
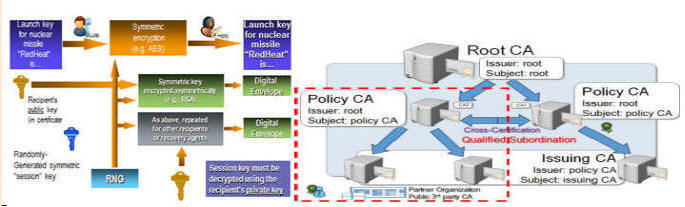
Public Key Infrastructure (PKI) using Asymmetric Cryptography—Homeland Security Presidential Directive 12 | Homeland [HSPD-12]
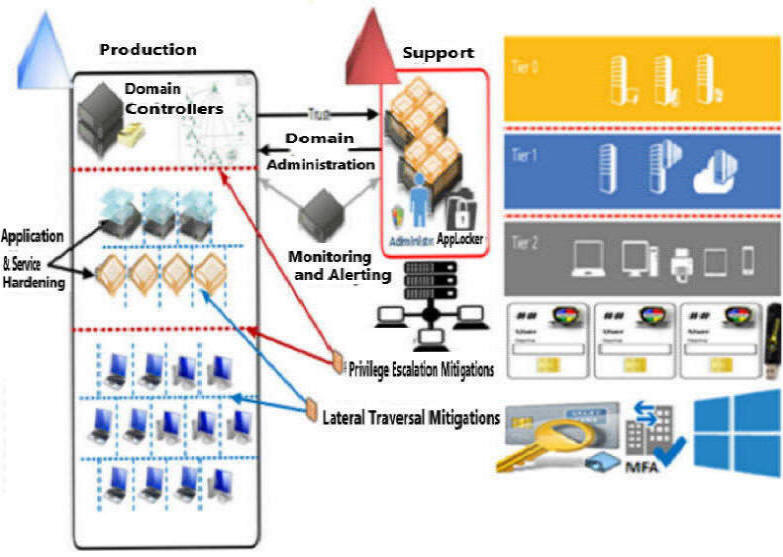
Isolate high Privilege Admin accounts from accessing lower privilege user workstations to effectively prevent cyber attacks which employ lateral traversal
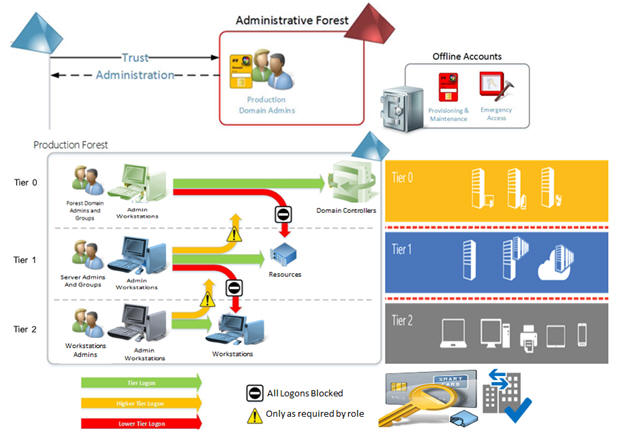
Create high Privilege Admin Account Workstations (PAW)

Related Services
An Infratac Consultant can assist creation of IT environments that are resilient to credential theft. Organizations' IT must also consider all aspects of credential usage and storage.
ü
Infratac
consultants can help your IT organization learn how to mitigate
lateral traversal attacks
ü
Learn how to
create models that isolate high privilege user accounts from regular
user accounts
ü
Learn how to
Create security hardened restricted administrative hosts.
ü
Learn Security
Information and Event Monitoring (SIEM)
ü
Learn
Cybersecurity Infrastructure concepts and principles
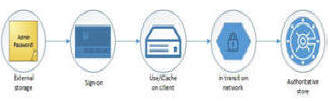





Click Ctrl+URL—Help avoid BIAS in Facial Recognition—of various ML | BI | AI | Algorithmic <ID> decision making processes and procedures!